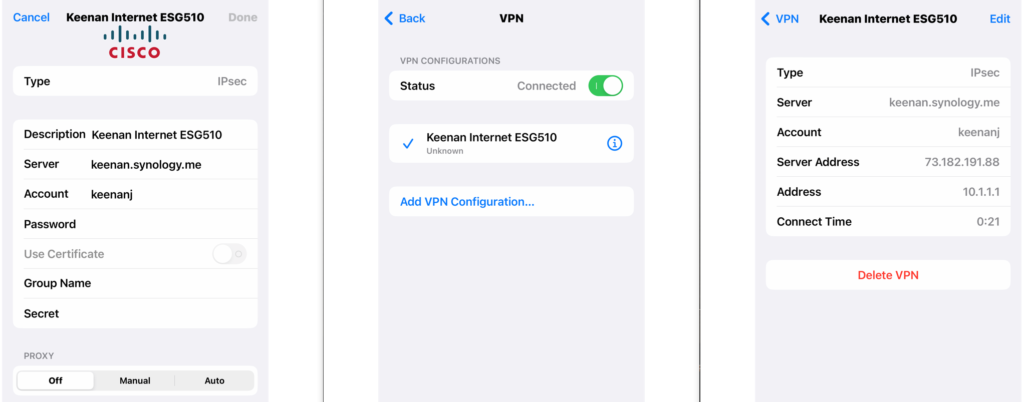
Although windows has a built in VPN client it frequently is not working due to updates you can use the free shrew soft VPN client with the ESG510.
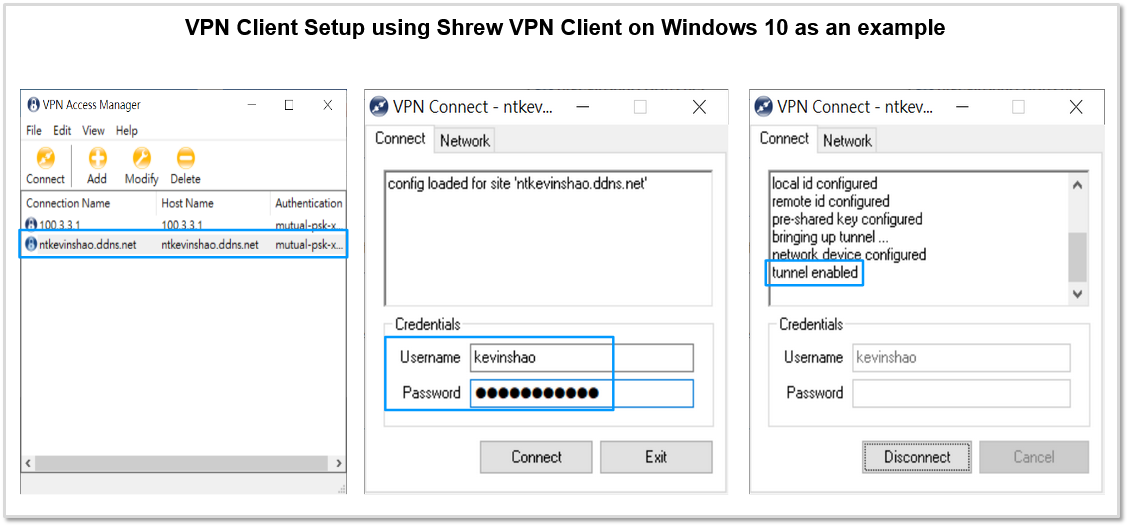
9.3 VPN Client using Shrew VPN Client on Windows 10 as an example
- This is an example of how the Shrew VPN client should be configured on a Windows 10 PC in order to launch a Client VPN connection to ESG.
- The screenshots in this slide and the next slides walk you through the configuration parameters on the Shrew VPN Client.
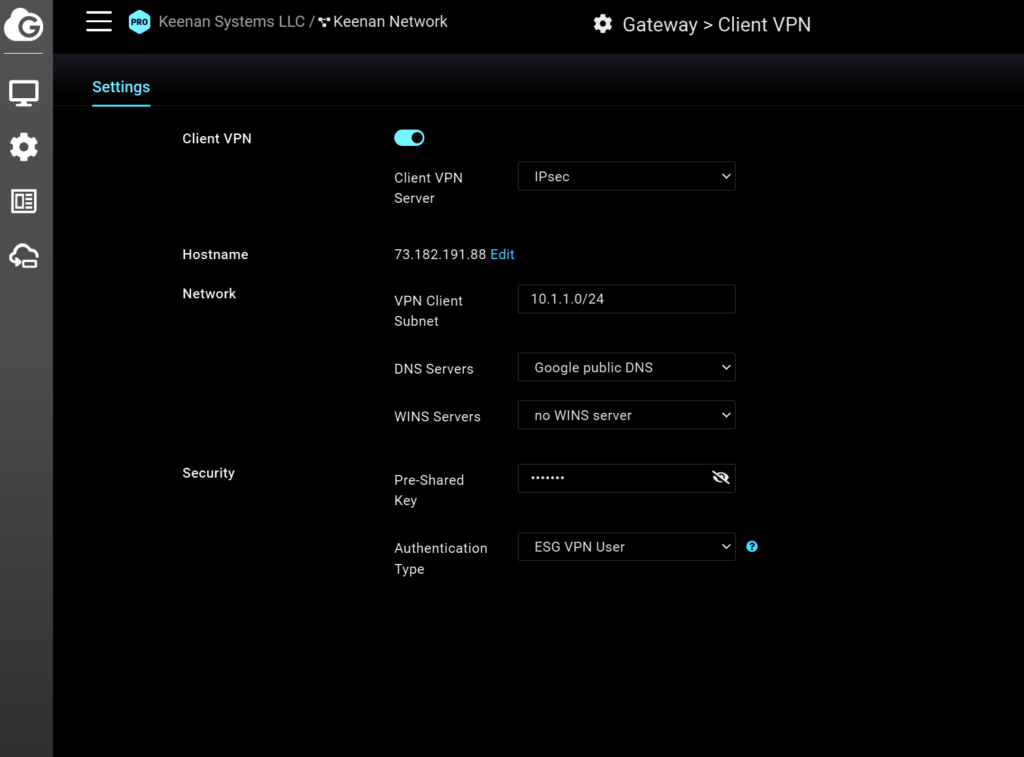
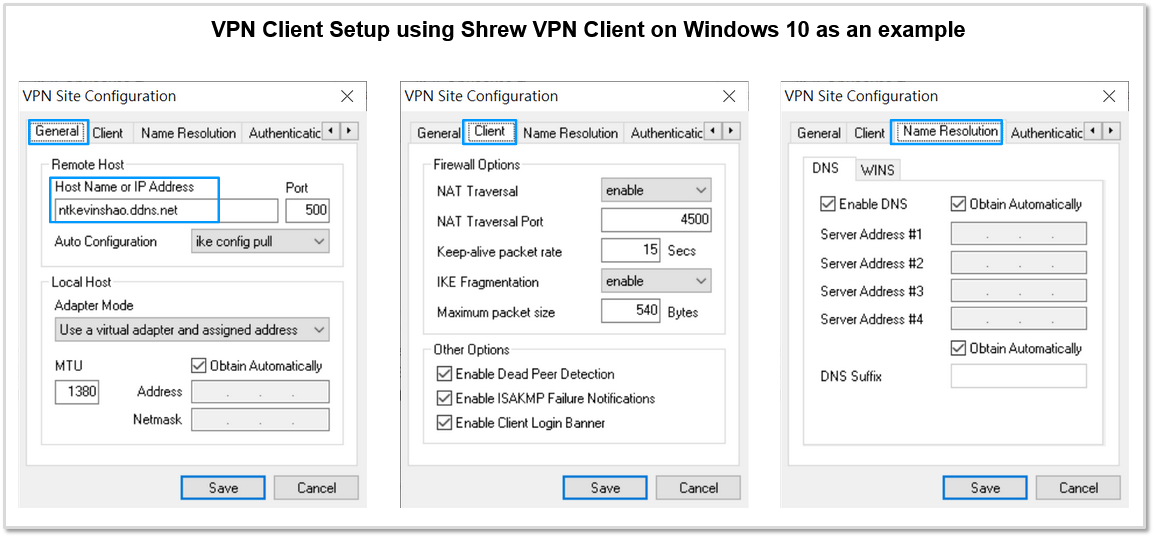
- Since my ESG WAN IP is not static, I have enabled the DDNS feature on ESG for hostname “ntkevinshao.ddns.net”, so ESG will report to ddns.net DNS server to use its Primary WAN Public IP for ntkevinshao.ddns.net DNS resolution. Therefore, I can input ntkevinshao.ddns.net in the Host Name or IP Address field without having to care what my ESG’s current WAN public IP is.
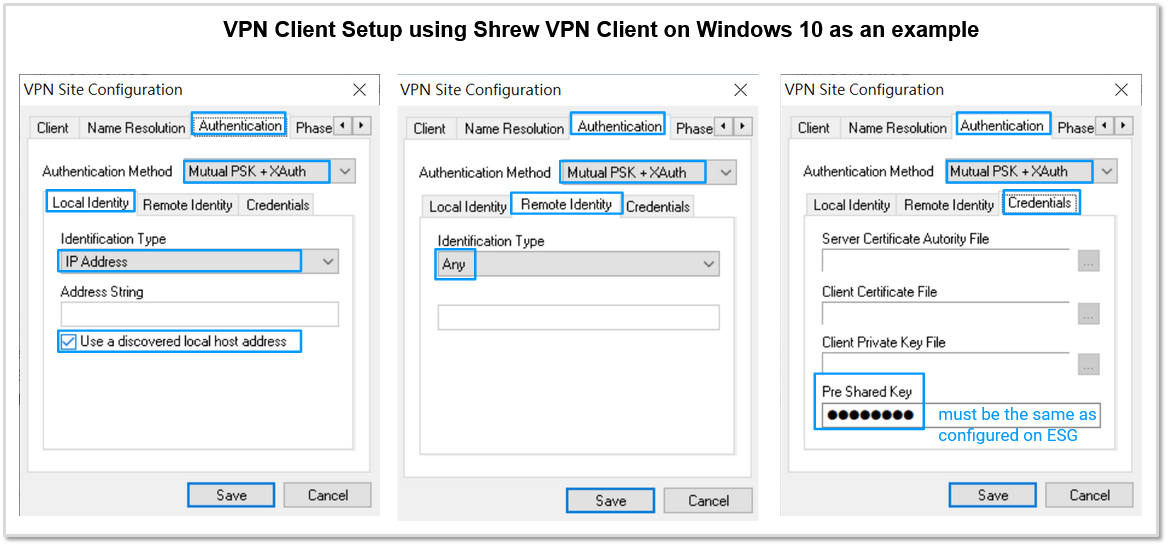
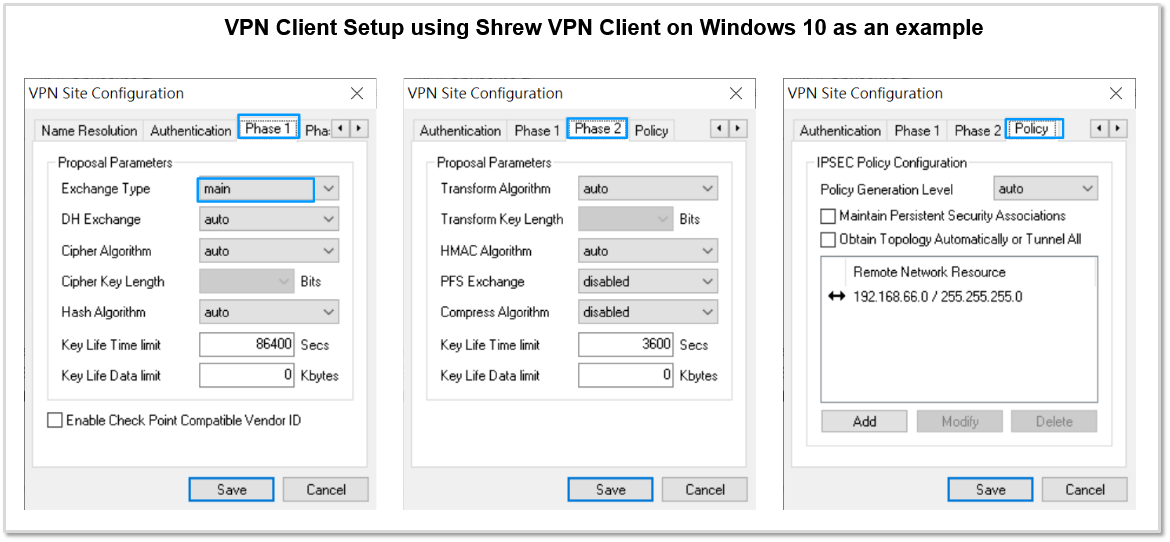
If you uncheck Obtain Topology Automatically or Tunnel All and specify Remote Network Resource manually, then Split Tunneling is used and only traffic with destinations matching the subnet(s) specified in Remote Network Resource are forwarded thru IPsec VPN tunnel.
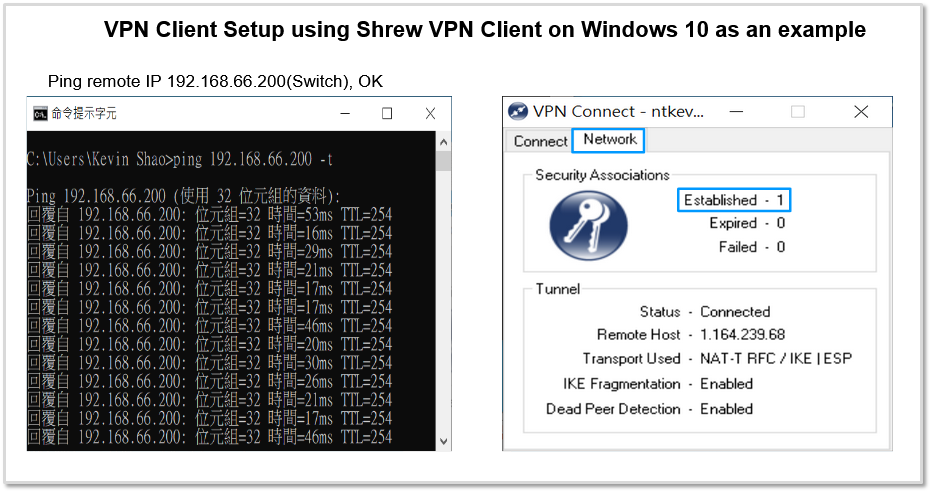
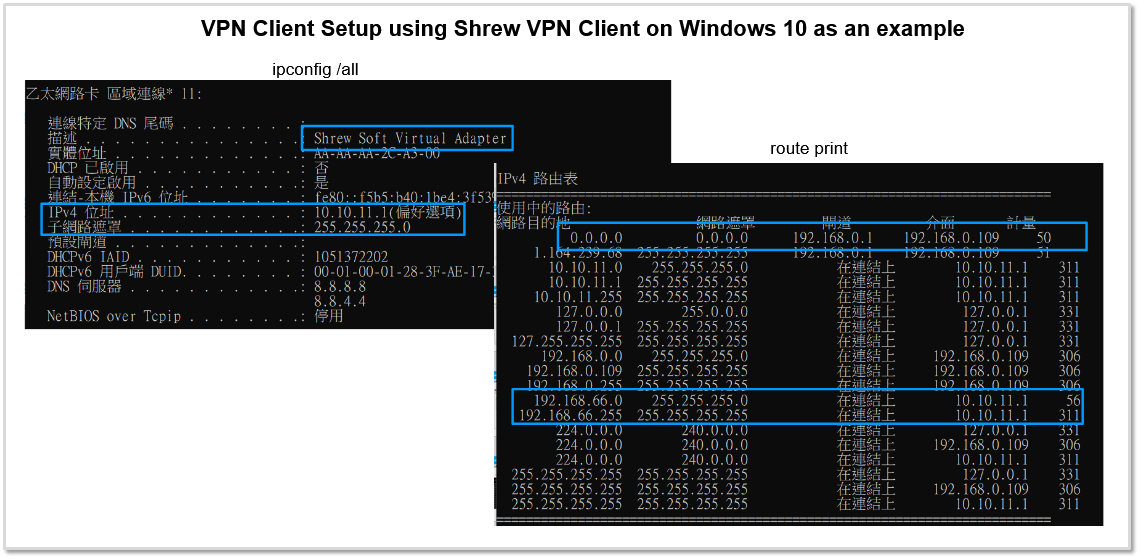
From the screenshot below, you can see client has got a 10.10.11.1 /24 IP address, default route is not changed but a static route to 192.168.66.0 /24 with next hop set to IPsec tunnel 10.10.11.1 is added because we had configured split tunneling in Shrew VPN client.